In the digital networking world, numbers like 172.16.252.214;4300 might look cryptic to most people, but for IT professionals and cybersecurity experts, they represent a specific combination of an IP address and port number that carries real meaning. To understand how systems communicate securely and efficiently, one must grasp how IPs and ports like these work together. Let’s break down what this combination means, its uses, and how it impacts networking environments.
What Does 172.16.252.214;4300 Represent?
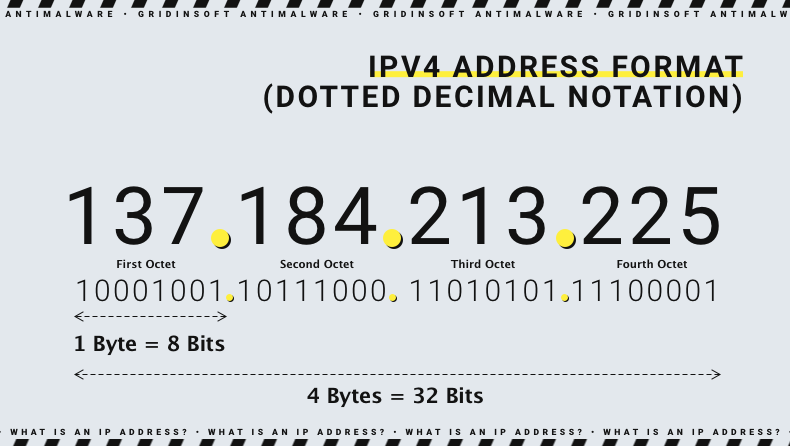
The sequence 172.16.252.214;4300 combines two key components of digital communication: the IP address 172.16.252.214 and the port number 4300. The IP address identifies a specific device within a network, while the port number specifies the exact service or application that the communication targets. Together, they create a unique path for data to travel from one point to another.
Understanding the IP Address Range
The IP portion, 172.16.252.214, belongs to the private IP range as defined by the Internet Assigned Numbers Authority (IANA). Private IPs are reserved for use within internal networks such as home routers, company LANs, or data centers. They are not accessible directly from the public internet, making them ideal for controlled, secure environments. This IP could belong to a server, workstation, or virtual machine operating inside a private infrastructure.
Private IP ranges, including 172.16.0.0 to 172.31.255.255, allow organizations to manage internal connectivity without consuming public IP resources. This helps prevent address conflicts and ensures scalability across corporate or enterprise-level systems.
The Role of Port 4300 in Network Communication
The semicolon and number that follow — ;4300 — represent the port number, which directs traffic to a specific service on the device. Ports range from 0 to 65535 and act as digital “doors” through which data enters or leaves a machine. For instance, web traffic typically passes through port 80 (HTTP) or 443 (HTTPS), while email or FTP use other predefined ports.
Port 4300 is not among the standard “well-known” ports, meaning it is often used for custom applications, internal services, or testing environments. In practice, an administrator might configure a private service — such as a local database, file-sharing system, or remote access tool — to operate on port 4300 to avoid conflicts with commonly used ports.
Common Use Cases of 172.16.252.214;4300
Because of its private IP designation, 172.16.252.214;4300 would typically exist within a closed environment like a corporate network. Some possible scenarios include:
-
Internal Database Communication: A secure internal database may use port 4300 for direct connections between applications.
-
Custom API Services: Developers might bind a custom API to this address and port to separate it from public endpoints.
-
Testing and Staging Environments: In software development, isolated test servers often use private IPs and non-standard ports to simulate production without exposing the system publicly.
-
IoT and Device Management: Smart devices or internal IoT controllers can also communicate through private IPs using specific ports for configuration or telemetry data exchange.
Security Implications and Best Practices
Although private IPs like 172.16.252.214 are shielded from the public internet, security is still essential. Internal threats, misconfigurations, or unauthorized access attempts can exploit open ports. Therefore, network administrators should adopt best practices such as:
-
Implementing firewall rules to restrict access to only necessary devices.
-
Regularly scanning internal ports for vulnerabilities.
-
Employing Network Address Translation (NAT) and VPNs to control connectivity.
-
Using strong authentication for services running on custom ports like 4300.
A well-secured network ensures that private systems remain isolated while still supporting smooth internal communication.
Why Understanding IP and Port Pairing Matters
In any digital ecosystem, understanding how IPs and ports interact is essential for maintaining performance, security, and efficiency. Combinations like 172.16.252.214;4300 are more than just random numbers — they are a blueprint of how data is structured and transmitted across systems. For professionals dealing with servers, networks, or cybersecurity, this knowledge provides insight into diagnosing issues, optimizing configurations, and preventing breaches.
Conclusion
The notation 172.16.252.214;4300 exemplifies how the digital world organizes communication between machines. It represents a private IP and a custom port that likely serve a specialized function within an internal system. While not publicly accessible, its correct configuration and security management are vital to ensuring a reliable and protected network. Understanding such pairings helps bridge the gap between technical theory and practical application — a skill every modern IT expert should master